What happend?
In the versions of the main plugin before 2.10.1 there was a vulnerability which allowed attackers to inject code in the option fields of the plugin. It was used mainly to inject ads.
The premium add-on was not affected.
Is it safe now?
Yes. I had the plugin checked by https://www.pluginvulnerabilities.com and everything is secure. You can find more details here: Audit Results
And wpscan confirmed the fix: https://wpscan.com/vulnerability/438c6818-cace-410b-ace3-325e5ea06365
Is the add-on affected as well?
NO. It is only the main plugin.
I am affected, what can I do?
Step 1: Update
Update to the newest version. This fixes the vulnerability and reduces the affects of the injected javascript. BUT the javascript still exists in the option fields. And this JS might cause the plugin not to work properly anymore.
Step 2: Clean the fields
You have to go through all the settings of the plugin to look for suspicious code. Mostly the json was affected in the “Im & Export section.”
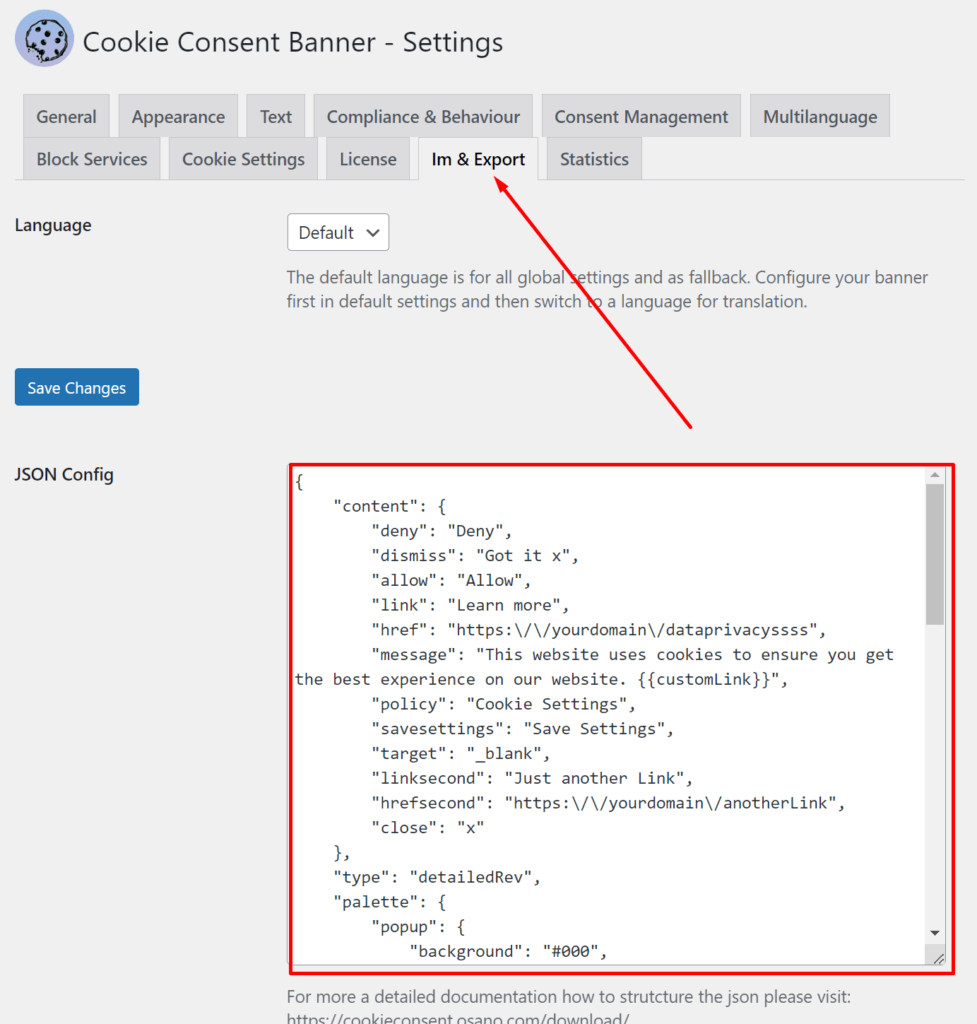
What I have seen so far, is that the complete settings string is corrupted. So you have to configure the plugin from scratch again.
You can use this default config: https://beautiful-cookie-banner.com/screens/config-default.json
Add the content to the “Im & Export” Area of the Plugin.
If you want to do checks in the database directly, you can use this query for it:
SELECT * FROM options
where
option_name like "%nsc_bar%"Step 3: Clear caches
Delete all your caches for example if you use a wordpress cache plugin or server cache like nginx.